“Organizations that automate security workflows see up to 30 % faster incident resolution and 40 % fewer manual errors.” Source
Today, security operations teams face an overwhelming volume of alerts from SIEM systems. Without proper automation and alignment with ITSM tools, many alerts languish unresolved or misrouted.
That’s where ServiceNow Microsoft Sentinel integration becomes a force multiplier — seamlessly turning Sentinel alerts into actionable ServiceNow incidents under a unified ServiceNow security automation framework.
In this guide, you’ll learn how to implement the integration step by step, with tips, quick notes, and a use-case focus, in a way that even a fresher in ServiceNow can follow. I’ll also introduce how you could extend this with an AI agent for intelligent routing and response.
What Is Microsoft Sentinel & Why Integrate with ServiceNow?
What is Microsoft Sentinel?
Microsoft Sentinel is a cloud-native SIEM (Security Information and Event Management) and SOAR platform that provides unified threat detection, investigation, and response across multi-cloud and hybrid environments.
It ingests logs, correlates alerts, triggers incidents, and supports automation workflows via playbooks (built on Azure Logic Apps).
Why integrate Sentinel with ServiceNow?
- Sentinel is great at detecting and generating alerts; ServiceNow is strong in workflow, assignment, audit trails, SLAs, and cross-team collaboration.
- Integration enables incident sync, comment sync, and status updates between SEC and IT teams.
- It reduces manual handoff, speeds up incident automation, enforces accountability, and helps in security incident response automation.
An AI agent in this workflow can act as a smart intermediary that, for example :-
- classifies alerts (based on past patterns),
- suggests assignment groups (based on historical mappings),
- adds contextual enrichment (from threat intel),
- auto–closes low-priority incidents or escalates.
With the ServiceNow–Sentinel connector in place, you’ll have the plumbing. The AI agent then layers intelligence over that plumbing to optimize routing, triage, and response.
Use Case Focus – Sentinel Alerts → Auto-Created SIR in ServiceNow
We will discuss the case study about when Microsoft Sentinel detects a threat and raises an incident, that incident is automatically ingested into ServiceNow’s Security Incident Response (SIR) module as a new security incident record. Updates (such as status changes or comments) sync back and forth.
Prerequisites & Planning Notes
Before you dive into configuration, ensure :-
- You have a ServiceNow instance with the Security Incident Response (SIR) plugin active (or relevant ITSM modules).
- You have an Azure/Microsoft 365 subscription and a Sentinel workspace enabled.
- You hold admin privileges in both ServiceNow (for plugin installs) and Azure AD (for app registration).
- You understand your field mapping needs (which Sentinel fields map to which ServiceNow fields).
- You have clarity on roles & permissions, and API quotas.
Quick note :- The Microsoft Sentinel-ServiceNow integration from the ServiceNow Store supports bidirectional sync (incident creation, updates, comment sync) via the Sentinel Management API.
But domain separation is a known limitation (the plugin does not support domain-separated instances)
Step-by-Step Setup
Here’s how to set up ServiceNow Microsoft Sentinel integration :-
Step #1 – Install the Sentinel Integration App in ServiceNow
- In ServiceNow, go to the ServiceNow Store and install the Microsoft Azure Sentinel – Incident Ingestion Integration for Security Operations app.
- Activate plugin dependencies (SIR, SecOps, etc.).
- Assign the sn_si.admin role to admin users to manage integration configuration.
Quick Tip :- After installation, navigate to “Azure Sentinel Integration > Profiles” in ServiceNow.
Step #2 – Register an App in Azure AD & Grant Permissions
- In Azure AD, go to App registrations → New registration.
- Name it (e.g., “Sentinel-to-SNOW”).
- Note the Application (client) ID and Directory (tenant) ID.
- Under Certificates & secrets, create a client secret (or use cert-based auth).
- In your Sentinel workspace’s Access control (IAM), assign the “Azure Sentinel Responder” role to this app registration.
- Also, ensure consent is granted for the necessary APIs (Sentinel Management API).
Important Note – When the client secret expires, you’ll need to update it in the ServiceNow integration config as well.
Step #3: Create a ServiceNow System User for the Integration
- In ServiceNow, go to User Administration → Users → New.
- Create a user specifically for integration (e.g. sn_azure_sentinel_user).
- Select “Web service access only” so that this user doesn’t appear in the UI login.
- Grant the roles sn_si.ingestion_profile_admin, sn_si.analyst, or other relevant roles.
This user will act as the “caller_id” when new incidents are created.
Step #4 – Configure the Integration Profile in ServiceNow
- Open Sentinel Integration → Profiles → New.
- Enter these details :-
- Name (e.g. “DefaultSentinelProfile”)
- Azure Tenant ID
- Client (app) ID
- Client Secret or certificate
- ServiceNow user (the system user you created)
- Define the ingestion schedule (how often to poll for new Sentinel incidents).
- Enable incident updates and closure syncing (for bidirectional).
- Save the profile.
Step #5: Map Sentinel Incident Fields to ServiceNow Fields
In the Field Mapping tab of your profile :-
- Map Severity → severity
- Map Title / Display Name → short_description or name
- Map Description → description
- Map Status / State → state / incident_state
- Map Entity lists, Observables, Comments → corresponding SIR fields
Optionally, enable “Override” flags so that updates from Sentinel always overwrite existing ServiceNow data for specific fields.
Tip – Keep mapping minimal at first; start with core fields, and extend later.
Step #6: Test Ingestion & Sync
- In Sentinel, create a sample incident (or wait for a real alert).
- Run the ingestion manually (or wait for the polling schedule).
- Verify :-
- A new incident appears in ServiceNow SIR.
- Fields (severity, description) match mapped values.
- Comments in Sentinel show up in ServiceNow work notes.
- If you update or close in ServiceNow, check if Sentinel is updated (if bidirectional sync is enabled).
If any field is missing or not syncing, revise your mapping or check connector permissions.
Troubleshooting & Tips
| Problem / Symptom | Likely Cause | Quick Fix / Note |
|---|---|---|
| Incident created but field values empty | Field mapping misconfigured | Revisit mapping tab in profile |
| Updates in ServiceNow not reflecting in Sentinel | Bidirectional sync not fully enabled, or API permission missing | Ensure “Enable updates” is toggled and app has rights |
| Integration errors or timeouts | Network/firewall or API throttling | Check logs, raise timeouts, scale polling intervals |
| Domain separation not working | Known limitation of plugin | Consider alternate custom Logic App route |
| Secret expired | Credential rotations | Update secret in profile promptly |
Extending with an AI Agent
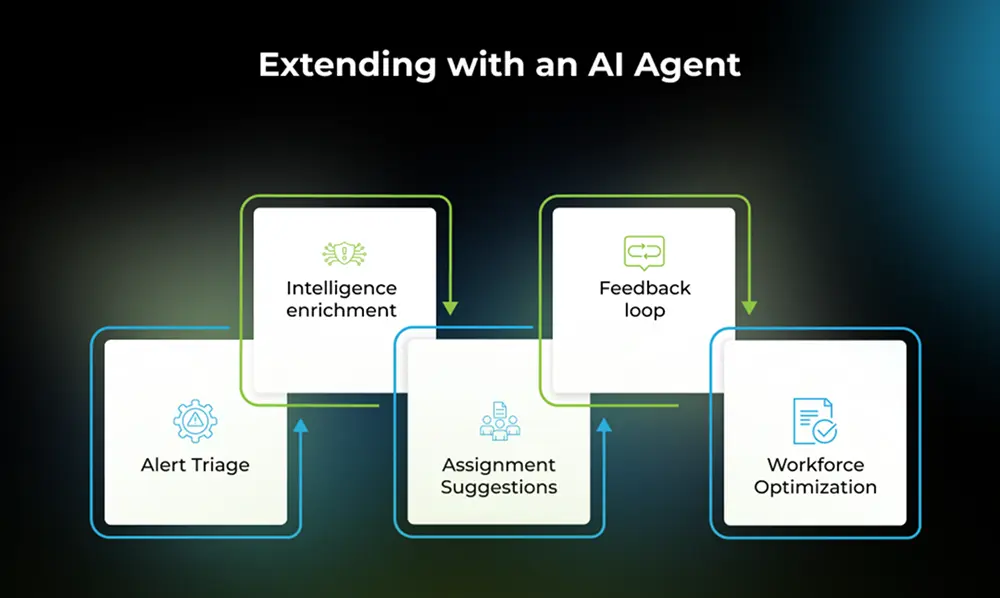
With the integration set, you can embed an AI agent to enhance automation :-
- Alert Triage :- The agent can classify whether an incident is a false positive or worth escalation based on past data.
- Assignment Suggestions :- Suggest the correct assignment group or analyst with high confidence.
- Auto-closure of low-risk incidents :- Close tickets if confidence is high and no further action is needed.
- Intelligence enrichment :- Pull threat intel, map IOCs, attach context, and update ServiceNow notes automatically.
- Feedback loop :- Learn from human remediation choices to improve suggestions.
Implementing the agent could be done using ServiceNow’s Virtual Agent framework, external AI services (e.g., OpenAI models), or on-prem ML pipelines. But you now have the foundation (integration + APIs) to plug it in.
Other Use Cases You Can Implement (Beyond the Main One)
| Use Case | Description | Value Delivered |
|---|---|---|
| ITSM Incident Creation | Create ITSM (non-security) incidents based on Sentinel alerts (e.g. firewall alerts) | Broaden integration beyond SIR, folds security alerts into IT flow |
| Threat Intel Sync | Sync IOC / threat intel from ServiceNow TISC into Sentinel rules | Keeps detection rules updated dynamically (via TISC) |
| Automated Playbooks | Use Microsoft Sentinel playbooks to call ServiceNow actions beyond incident creation (e.g. change config, isolate host) | More active response workflows |
| Case Enrichment | After ticket creation, fetch additional asset or user data from ServiceNow CMDB | Improves triage with contextual info |
| Two-way comment sync | Analysts can comment in ServiceNow or Sentinel and have notes appear in both systems | Better collaboration & audit trail |
| Auto-Resolve Low-Priority Alerts | Use thresholds to auto-close less critical alerts without human intervention | Reduces noise and manual workload |
FAQs on ServiceNow–Microsoft Sentinel Integration
1. Can I use this integration in ServiceNow’s ITSM (Incident Management), not Security Incident Response?
Yes, but the built-in Sentinel integration app is primarily designed for Security Incident Response (SIR). Some organizations build custom bridging logic (via Logic Apps or scripting) to post alerts into ITSM incident tables.
2. Does the integration support domain separation in ServiceNow?
No — the official Microsoft Sentinel integration plugin currently does not support domain-separated instances. That’s a documented limitation.
3. How often is data synced between Sentinel and ServiceNow?
You can configure a polling schedule (every few minutes, hourly, etc.). The integration supports scheduled ingestion and updates/closure polling depending on the profile settings.
Also Reads :-
SolarWinds ServiceNow Integration – A Step-by-Step Guide for Beginners (with Real Code Examples)
Final Thoughts
You’ve now seen how to integrate ServiceNow with Microsoft Sentinel — from installing the plugin, registering the Azure app, configuring profiles, mapping fields, to running tests. We also touched on extending with an AI agent and multiple real-world use cases.
This integration empowers SOC teams to automate and synchronize security alerts and incidents, bridge communication between IT and security, and reduce manual toil — all while maintaining audit trails and SLAs.
If you’re ready to take your ServiceNow–Sentinel integration to production — and layer AI-driven automation on top, LMTEQ is your ideal partner. We are a preferred consulting and implementation partner (specialist level) with specialization in AI and security integrations.
Reach out to us, and let’s modernize your security workflows together.
